There is no denying there is a significant lack of privacy online. Once the information is out there, anyone can access it! Did you know that the telecommunications sector is the most vulnerable to cyber attacks regarding data?
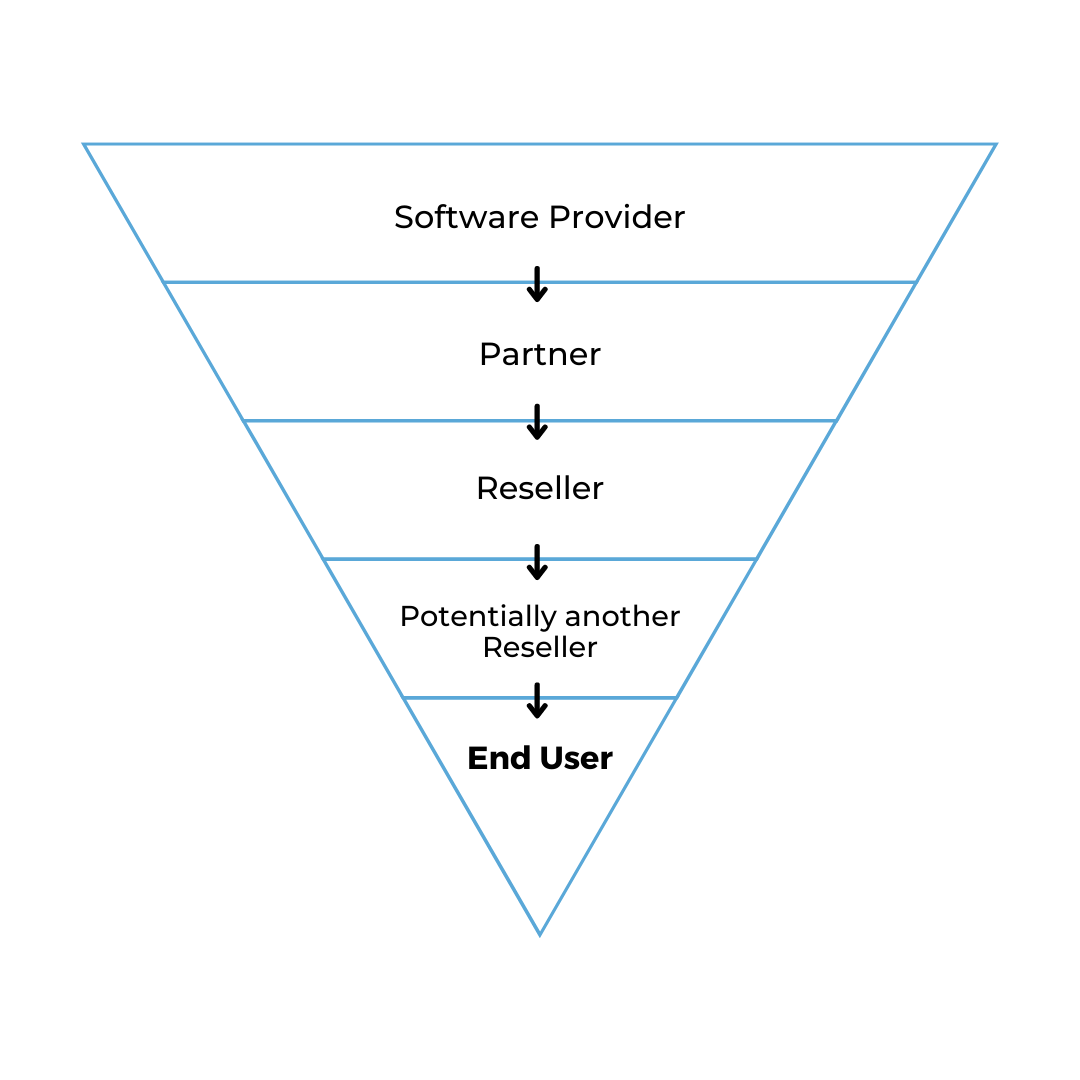 The telecom industry is a gold mine for hackers! The industry is like a funnel, with the top being the provider and the bottom the end-user. Providers have information on their partners, and the partners have information on their customers and so on.
The telecom industry is a gold mine for hackers! The industry is like a funnel, with the top being the provider and the bottom the end-user. Providers have information on their partners, and the partners have information on their customers and so on.
Once a hacker gains access, they can see data of each section in the funnel. Imagine all the private information like phone numbers, basic contact info, credit card numbers, addresses, and more! Like we said, gold mine.
If you are in the telecommunications industry or a fan of protecting your data, take a look at our best practices.
“If you’re an employee, you are on the front lines of information security.”
Clear Your Browser Data
Do any of my Office fans remember when Andy was trying to get a new computer and did everything in his power to break his current one?
“Allow all cookies? Why certainly!”
The odds Andy knew what he was allowing are slim. Web browsers and websites routinely collect and retain data about yourself and your online activities. Once the data is collected, it often is passed to third parties.
It is crucial to clear your cache and cookies regularly! Users can even configure their browser to protect them from tracking or use alternate search engines that do not collect data.
Password Protection
At this point, with technology, using a strong password is common sense. But if you are reusing the same password and a hacker accesses your Facebook account, they will soon gain entry into your online banking, e-mail, and more! Many believe that once they think of one strong password, they can use it for all accounts – but that is not the case.
Always use a unique password for each account you create. Store the passwords in a secure location and do not share them with anyone else. On top of that, for double protection, users should take advantage of two-step verification.
The two-step verification process ensures that even if a cyber attacker gets your password, they can not access your accounts. After inputting your password, a numerical code will send to your verification application on your smartphone. After inputting the code, you will have access to your account. Whenever possible, consistently implement a two-step verification.
Backup Your Data
Regularly backing up your data is the most important practice you can do to protect your information. There are two ways you can backup your data, Offline or Online.
An Offline backup means you are backing up to an external drive like an HDD or SSD versus an Online backup that backs up your data to a secured cloud. The recommended option is to backup offline to an external hard drive because you will still have access to your data in a secured location in the event of a significant breach or disaster.
If you do not want to invest in external hard drives, the alternative option is to backup online to the cloud. More often than not, cloud providers invest millions of dollars to achieve the highest form of security to keep their customers’ data safe.
Regardless of the option you choose, it is vital to backup your data!
To Conclude
As per Gartner, 65% of the world’s population will have their data covered under a regional or global privacy regulation by 2023. Companies must develop new approaches that abide by the rules but still give them viable data. By 2023, new practices for data protection may be available!


